- Password Encrypted Folder
- How To Decrypt Encrypted Password
- Decrypt Password
- Juniper Encrypted Password Crack 1 6
- How To Crack Encrypted Password
Theses hashes are visible in configuration and starts with '$1$'. On the other hand the TACACS+ / Radius Server key and VPN Pre-shared key are stored in reversible encyption hashes and these hashes starts with $9$ (Sample config att). The reversible encryption hashes are easily decrypted to origional keys using online available tools. It starts with $1$ and requires brute-force technique to recover the password; Juniper $9$ Password: These passwords are encoded using Juniper's private encryption algorithm. Password hash starts with $9$ text & can be decrypted instantly. You can use Juniper Password Decryptor tool to quickly decrypt these Juniper $9$ passwords. It supports dual mode of password recovery. You can either enter the encrypted Juniper. Sha-1 is a cryptographic function that takes as input a 2^64 bits maximum length message, and outputs a 160 bits hash, 40 caracters. Sha-1 is an improvement of Sha-0, it was created by the NSA, and improve cryptographic security by increasing the number of operations before a collision (theory says 2^63 operations), however Sha-1 is not considered as secure because 2^63 could be reach pretty. M Series,MX Series,PTX Series,T Series,SRX Series. Use to display plain text versions of obfuscated ($9) or encrypted ($8) passwords. If the password was encrypted using the new $8$ method, you are prompted for the master password. Screenshot 1: Juniper Password Decryptor is showing the recovered Password from the encrypted Juniper $9$ Password: Screenshot 2: Showing Password recovered from the Juniper configuration file. Disclaimer 'Juniper Password Decryptor ' is designed with good intention to recover the Lost Router Password.
This page will help you to differentiate the two hashing methods used in MySQL databases (all versions).
The biggest change was done with version 4.1, when they introduced a stronger hashing algorithm based on SHA-1.
Prior to MySQL v4.1, password hashes computed by the PASSWORD() function are 16 bytes long. Such hashes look like this:
This hash is commonly called 'mysql323' as this is the last version of MySQL to use this kind of hash.
The 4.1 (and upper) Hashing Method
MySQL 4.1 introduced password hashing that provided better security and reduced the risk of passwords being intercepted. There were several aspects to this change:
- Different format of password values produced by the PASSWORD() function
- Widening of the Password column
- Control over the default hashing method
- Control over the permitted hashing methods for clients attempting to connect to the server
- Password hashes in the 4.1 format always begin with a '*' character, whereas passwords in the pre-4.1 format never do.
- MySQL 4.1.0 used a preliminary version of the 4.1 hashing method. This method was short lived and the following discussion says nothing more about it.
- In MySQL 4.1.1, the hashing method was modified to produce a longer 41-byte hash value:

Password Encrypted Folder
For developpers, a MySQL hash can be computed with :
You can paste your mysql323 hash (16-bytes) or MySQl 4.1/5+ hashes (40-bytes, without '*' !) in our system.
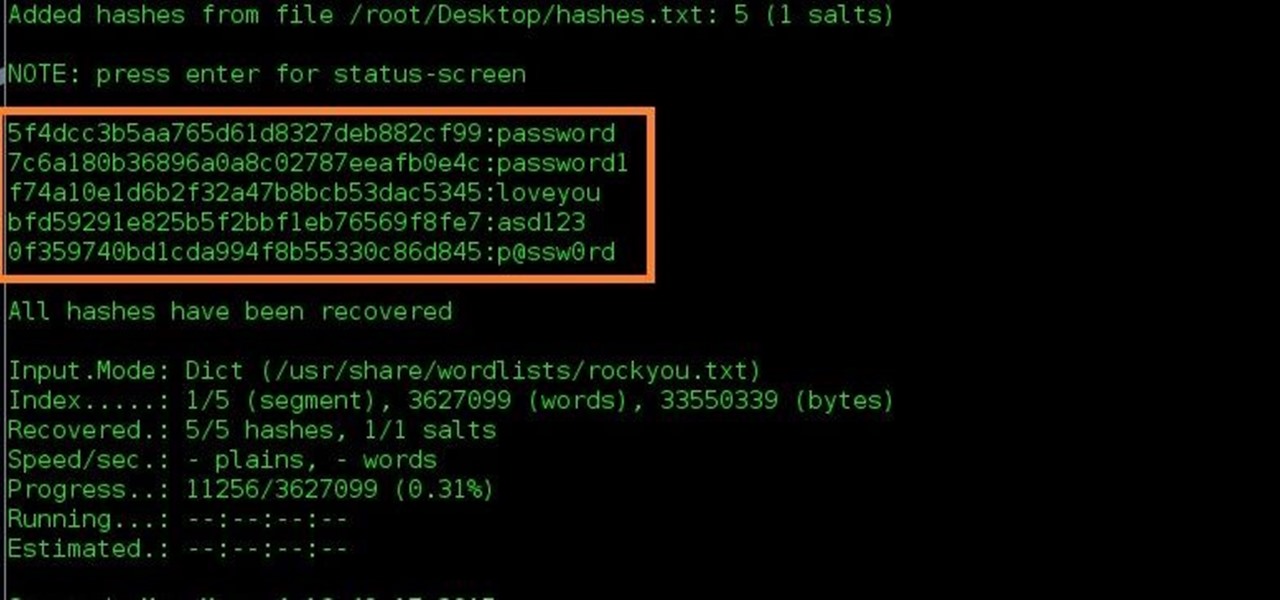
Note : This website can crack 100% of your 'MySQL323' 16-bytes hashes. Bruteforce or/and collision are used.
How To Decrypt Encrypted Password
Bonus
Google dork.
Decrypt Password
Have you ever wondered how Junos stores your passwords in configuration? And is there a difference between this one:

- Password Encrypted Folder
- How To Decrypt Encrypted Password
- Decrypt Password
- Juniper Encrypted Password Crack 1 6
- How To Crack Encrypted Password
Theses hashes are visible in configuration and starts with '$1$'. On the other hand the TACACS+ / Radius Server key and VPN Pre-shared key are stored in reversible encyption hashes and these hashes starts with $9$ (Sample config att). The reversible encryption hashes are easily decrypted to origional keys using online available tools. It starts with $1$ and requires brute-force technique to recover the password; Juniper $9$ Password: These passwords are encoded using Juniper's private encryption algorithm. Password hash starts with $9$ text & can be decrypted instantly. You can use Juniper Password Decryptor tool to quickly decrypt these Juniper $9$ passwords. It supports dual mode of password recovery. You can either enter the encrypted Juniper. Sha-1 is a cryptographic function that takes as input a 2^64 bits maximum length message, and outputs a 160 bits hash, 40 caracters. Sha-1 is an improvement of Sha-0, it was created by the NSA, and improve cryptographic security by increasing the number of operations before a collision (theory says 2^63 operations), however Sha-1 is not considered as secure because 2^63 could be reach pretty. M Series,MX Series,PTX Series,T Series,SRX Series. Use to display plain text versions of obfuscated ($9) or encrypted ($8) passwords. If the password was encrypted using the new $8$ method, you are prompted for the master password. Screenshot 1: Juniper Password Decryptor is showing the recovered Password from the encrypted Juniper $9$ Password: Screenshot 2: Showing Password recovered from the Juniper configuration file. Disclaimer 'Juniper Password Decryptor ' is designed with good intention to recover the Lost Router Password.
This page will help you to differentiate the two hashing methods used in MySQL databases (all versions).
The biggest change was done with version 4.1, when they introduced a stronger hashing algorithm based on SHA-1.
Prior to MySQL v4.1, password hashes computed by the PASSWORD() function are 16 bytes long. Such hashes look like this:
This hash is commonly called 'mysql323' as this is the last version of MySQL to use this kind of hash.
The 4.1 (and upper) Hashing Method
MySQL 4.1 introduced password hashing that provided better security and reduced the risk of passwords being intercepted. There were several aspects to this change:
- Different format of password values produced by the PASSWORD() function
- Widening of the Password column
- Control over the default hashing method
- Control over the permitted hashing methods for clients attempting to connect to the server
- Password hashes in the 4.1 format always begin with a '*' character, whereas passwords in the pre-4.1 format never do.
- MySQL 4.1.0 used a preliminary version of the 4.1 hashing method. This method was short lived and the following discussion says nothing more about it.
- In MySQL 4.1.1, the hashing method was modified to produce a longer 41-byte hash value:
To accommodate longer password hashes, the Password column in the user table was changed at this point to be 41 bytes, its current length.
Password Encrypted Folder
For developpers, a MySQL hash can be computed with :
You can paste your mysql323 hash (16-bytes) or MySQl 4.1/5+ hashes (40-bytes, without '*' !) in our system.
Note : This website can crack 100% of your 'MySQL323' 16-bytes hashes. Bruteforce or/and collision are used.
How To Decrypt Encrypted Password
Bonus
Google dork.
Decrypt Password
Have you ever wondered how Junos stores your passwords in configuration? And is there a difference between this one:
and this one:
Actually, the difference is significant: $1 passwords are 'salted' SHA-1 hashes ('salted' means – the calculated hash is different every time, even if the password is the same), and the $9 passwords are just scrambled ones and can be easily reverted to the original plain-text form.
Juniper Encrypted Password Crack 1 6
There is an online tool for that, or if you prefer a locally working script, there are some on the Internet, such as this one (Python 2 and 3):
How To Crack Encrypted Password
In conclusion, although user's passwords ($1 ones) can't be easily recovered from a leaked config, your protocol authentication, FTP password, RADIUS secret, IKE pre-shared key, and some other sensitive keys can be derived from it. So make sure to keep your config backups in a secure place.
