- Centos Wake On Lan
- Proxmox 6 Wake On Lan
- Wake On Lan Debian
- Proxmox Enable Wake On Lan
- Supports Wake-on D
The Status Report tab in Firebox System Manager contains the Firebox Status Report. This report includes information about all the currently active processes on your Firebox, the ARP table, interface and routing metrics, and other information about the current status and configuration of your device. You can use the Status Report to monitor the performance of your Firebox and the traffic through the device. You can also use the Status Report when you work with WatchGuard Technical Support to troubleshoot issues.
Supports Wake-on: pumbg Wake-on: g. Which looks right to me. Earthw0rmjim: 10:37 AM: Seems WOL is enabled by default. In this case you don't have to touch init.d. All you have to do is make sure WOL is enabled in the BIOS, then you can use it. The target computer's motherboard and Network Interface Controller have to support Wake-on-LAN. The target computer has to be physically connected (with a cable) to a router or to the source computer for WoL to work properly. Some wireless cards have support for Wake on Wireless (WoWLAN or WoW). Supports Wake-on: pumbg. We really only care to see that this line contains a 'g', indicating a that it will accept a 'magic packet' (the mechanism by which wake-on-LAN works). N.B.: If you don't see it, all hope is not lost, you may just need to enable 'Wake-On-LAN' in the BIOS. The -wol option is used to set ' Wake-on-LAN ' options. Not all devices support this. Not all devices support this. The argument to this option is a string of characters specifying which options to enable. Not all devices support this. The argument to this option is a string of characters specifying which options to enable. P Wake on PHY activity u Wake on unicast messages m Wake on multicast messages b Wake on broadcast messages a Wake on ARP g Wake on MagicPacket™ s Enable SecureOn™ password for MagicPacket™ d Disable (wake on nothing).
The sections in this example are from a WatchGuard XTM 1050 Status Report. If you have a different Firebox model, or have different features enabled on your device, your Status Report can include different information.
Uptime, Version, and Serial Number Information
At the top of the Status Report, the system time, uptime for the Firebox, and the version numbers of the major software components appear. The serial number and model number of the device are also included.
Firebox Components Status
The Firebox Modular Components section contains the version number and build information for each Fireware XTM module on the Firebox .
In this example, the modules are version 11.9.
Logging
The Log Configuration section contains information about whether logging is enabled to a syslog server or WatchGuard Log Server, and the IP addresses of any configured Log Servers.
To configure these settings, from Policy Manager, select Setup > Logging.
If your device is configured to send log messages to a syslog server, because the traffic from the device to the syslog server is sent only one way, and because the connection to the syslog server is not confirmed by the device, the Status setting that appears is always Connected.
If your device is configured to send log messages to a WatchGuard Log Server, the Status only appears as Connected if the connection to the WatchGuard Log Server or Dimension is active and the Log Server accepts the log messages sent from the device. If a WatchGuard Log Server is configured for your device but the Status that appears is Disconnected, the IP address or authentication key specified in the device configuration for the Log Server might be incorrect.
Process List
The Process List section of the Status Report contains information about all the current processes on the Firebox.
The example below is a partial list. Your Status Report might include information about more processes.
Each line in the process list includes this information:
PID
The process ID.
ST
Process status codes. These are the possible status codes:
D — Uninterruptible sleep (usually IO)
R — Runnable (on run queue)
S — Sleeping
T — Traced or stopped
Z — A defunct ('zombie') process
W — Has no resident pages
< — High-priority process
N — Low-priority task
L — Has pages locked into memory (for real-time and custom IO)
I — Uninterruptible idle (does not contribute to load average)
%CPU
The percentage of CPU capacity used by this process.
VSS
Virtual memory usage.
RSS
Real memory usage.
SHARED
Shared memory usage.
STARTED
What time the process started.
TIME
The total CPU time this process used.
COMMAND
The name of the process or command.
Memory
The amount of Firebox memory currently in use appears in the Memory info section of the Status Report.
To understand how much available memory your Firebox has, review these memory statistics, available in the Status Report:
MemTotal
This is the total amount of memory available on your device.
MemFree
This is the amount of memory that is not reserved or currently in use.
Buffers
This is the amount of memory the Firebox has reserved for temporary use by all Firebox processes.
Cached
This is the amount of memory that is reserved by device processes, but not currently in use. A high Cached value does not indicate a memory problem.
A low MemFree value does not indicate a problem with Firebox performance or resources. The total available memory for the Firebox is the combined value of MemFree, Cached, and Buffers.
To improve system performance, Fireware allocates most available memory to buffers and cache. If a process requires more memory, Fireware automatically frees up memory used by buffers and cache.
Load Average
The Load Average section contains statistics about average process load over time.
The Load Average shows the number of jobs in the processor core run-queue, or the run-queue length. The run-queue length is the total number of processes currently running, plus the number of processes that are on hold in the run-queue. If the Load Average values are high, the system is under heavy use and the response time is correspondingly slow.
1-min
This number is the average load for the last minute.
5-min
This number is the average load for the last 5 minutes.
15-min
This number is the average load for the last 15 minutes.
run-proc
This statistic has two numbers: the first number is the number of processes in the run state; the second number is the total number of processes on the device. In this example, the run-proc is 2/52, which means there are 2 current processes from a total of 52 on the Firebox .
last-pid
This value is the PID (process ID) that is assigned to the next process.
For example, if your Firebox has eight cores and a Load Average of 4.0, the device would not be under heavier use than a device with one core and a Load Average of .5.
IPv6 Network Hop Limit
The IPv6 Network Hop Limit section includes the current IPv6 hop limit settings configured for the interfaces on your device. The hop limit is the number of network segments a packet can travel over before it is discarded by a router. The default value is 64.
Network Configuration

The status of physical network interfaces on the Firebox appears in the Network Configuration section.
For each interface, the Status Report indicates whether the interface is enabled, the name of the interface, and the IP address. It also shows the Maximum Transmission Unit (MTU), the status of the interface (up or down), and whether the IP address assignment is static or dynamic.
Enabled
Yes or No. This indicates whether the interface is currently enabled in the Firebox or XTM configuration
IF-#
This is the number assigned to the interface. A wireless interface ath1, physical interface eth1, and virtual interface vlan1 can all be assigned the number 1.
Dev-Name
The name of the interface as it appears in Fireware OS. The interface name also appears in some Event and Debug log messages.
- eth# — A physical interface on the Firebox.
- ath# — A wireless interface on the Firebox. This only applies to wireless interfaces on the Firebox, not interfaces with a connected AP device.
- vlan# — A Virtual LAN interface and the VLAN ID number.
- bond# — A Link Aggregation interface.
- br# — A bridge interface on the Firebox.
Name
The name specified for the interface. This is included in traffic log messages in Traffic Monitor.
Address
The primary IP address of the interface, in CIDR format. Secondary IP addresses do not appear in this section.
Centos Wake On Lan
Zone*/MTU
The network zone, such as TR (trusted), EX (external), or OP (optional), and the MTU value configured for the interface.
Status
up or down. This indicates the status of the physical link or Multi-WAN interface.
IP-Assignment
Proxmox 6 Wake On Lan
static, dhcp, or pppoe. This shows how the interface is assigned an IP address.
Interfaces
Configuration information and traffic statistics for each Firebox network interface appear in this section.
If a colon (:) appears in an interface number, it indicates a secondary network (interface alias). A period (.) in an interface number, indicates a VLAN interface. The number after the period(.) is the VLAN ID number.
Interfaces that appear in your report with names such as br1 and br2 are bridges (virtual interfaces) associated with the two VLANs on eth3,1 and eth3, 2.
A lo interface is a loopback virtual interface. This interface has the standard loopback IP address of 127.0.0.1. Packets destined for this network loop back to the Firebox .
An interface such as tun0 is a Point-to-Point VPN tunnel virtual interface.
An interface such as bond0 is a link aggregation interface.
An interface such as ath0 is a wireless interface.
An interface such as gre0 is a virtual interface related to Branch Office VPN tunnels.
An interface such as sw10 is a virtual switch interface which is used by some Firebox models to manage physical interfaces.
Each line of the status for each interface includes this information:
Interface description
Interface name, interface type, MAC address
IP Address information
The status of physical network interfaces on the Firebox appears in the Network Configuration section.
For each interface, the Status Report indicates whether the interface is enabled, the name of the interface, and the IP address. It also shows the Maximum Transmission Unit (MTU), the status of the interface (up or down), and whether the IP address assignment is static or dynamic.
Enabled
Yes or No. This indicates whether the interface is currently enabled in the Firebox or XTM configuration
IF-#
This is the number assigned to the interface. A wireless interface ath1, physical interface eth1, and virtual interface vlan1 can all be assigned the number 1.
Dev-Name
The name of the interface as it appears in Fireware OS. The interface name also appears in some Event and Debug log messages.
- eth# — A physical interface on the Firebox.
- ath# — A wireless interface on the Firebox. This only applies to wireless interfaces on the Firebox, not interfaces with a connected AP device.
- vlan# — A Virtual LAN interface and the VLAN ID number.
- bond# — A Link Aggregation interface.
- br# — A bridge interface on the Firebox.
Name
The name specified for the interface. This is included in traffic log messages in Traffic Monitor.
Address
The primary IP address of the interface, in CIDR format. Secondary IP addresses do not appear in this section.
Centos Wake On Lan
Zone*/MTU
The network zone, such as TR (trusted), EX (external), or OP (optional), and the MTU value configured for the interface.
Status
up or down. This indicates the status of the physical link or Multi-WAN interface.
IP-Assignment
Proxmox 6 Wake On Lan
static, dhcp, or pppoe. This shows how the interface is assigned an IP address.
Interfaces
Configuration information and traffic statistics for each Firebox network interface appear in this section.
If a colon (:) appears in an interface number, it indicates a secondary network (interface alias). A period (.) in an interface number, indicates a VLAN interface. The number after the period(.) is the VLAN ID number.
Interfaces that appear in your report with names such as br1 and br2 are bridges (virtual interfaces) associated with the two VLANs on eth3,1 and eth3, 2.
A lo interface is a loopback virtual interface. This interface has the standard loopback IP address of 127.0.0.1. Packets destined for this network loop back to the Firebox .
An interface such as tun0 is a Point-to-Point VPN tunnel virtual interface.
An interface such as bond0 is a link aggregation interface.
An interface such as ath0 is a wireless interface.
An interface such as gre0 is a virtual interface related to Branch Office VPN tunnels.
An interface such as sw10 is a virtual switch interface which is used by some Firebox models to manage physical interfaces.
Each line of the status for each interface includes this information:
Interface description
Interface name, interface type, MAC address
IP Address information
Interface IP address, broadcast IP address, IP netmask
Interface status information
Interface status flags (this includes: UP, BROADCAST, MULTICAST, and others)
Interface MTU (in bytes)
Interface metric (priority)
Received packet statistics
Number of received packets
Number of receive errors (this includes jabber, CRC, buffer overrun, runt frames, and others)
Number of dropped RX packets (these are rare)
Number of FIFO overruns (these are rare)
Number of frame errors (see note below)
Transmit packet statistics
Number of transmitted packets
Number of transmit errors (generally only transceiver problems)
Number of dropped packets (these are uncommon)
Number of FIFO overruns (these are uncommon)
Number of carrier errors (generally indicate bad Ethernet hardware or bad cabling)
Collisions statistics and transmit queue length
Number of collisions and transmit queue length
Transmit and receive byte counts
Number of bytes transmitted and received
Interrupt and memory
Interrupt and memory address for this interface
A high number of errors (greater than .1% of total packets) can be caused by bad Ethernet connectivity between the Firebox and what it is connected to, or it can be caused by hardware failure.
Frame errors are Ethernet errors that fail the Cyclic Redundancy Check (CRC) of the Ethernet receiver. These errors indicate damaged frames. There can be many causes for frame errors. For example, bad wiring, broken Ethernet hardware, and cable runs that are too long.
Physical Interfaces Link Status
The Physical Interfaces Link Status section includes link information for each interface on your device.
Other areas that can appear in the Physical Interfaces Link Status section of the report include:
Wireless
This section includes the wireless options enabled for each wireless adapter on your Firebox, and the interface information for any active wireless network on your device. The interface information should correspond to the wireless interfaces enabled on your device.
Bridges
This section shows the bridges enabled to the interfaces on your device, and includes any VLANs and the interface name.
For example, if your device has a wireless network bridged to a physical interface, an entry like this could appear in the Bridges section:
Bridge MACs
This sections includes the MAC address for each member interface on your device that is configured as a LAN bridge. Bridges from a wireless network to an interface are not included in this section.
Routes
Routes are included in two separate tables: IPv4 Routes and IPv6 routes.
For more information about route tables, see Read the Firebox Route Tables.
IPv4 Routes
The IPv4 Routes section includes this information for the first 100 IPv4 routes:
- Destination — The destination IP address for the route
- Gateway — The IP address of the gateway the route uses.
- Genmask — The subnet mask for the destination IP address
- Flags — Route flags that indicate characteristics of the route.
- Metric — The routing metric, or cost for the route. A lower number indicates a lower cost and higher route priority.
- Interface — The interface to which packets for this route will be sent. For example, eth0 for interface 0.
This information appears for IPv4 static, dynamic, connected, and BOVPN virtual interface routes.
IPv6 Routes
The IPv6 Routes section includes this information for the first 100 IPv6 routes:
- Destination — The destination IP address for the route
- Next Hop — The IP address of the next hop for the route.
- Flags — Route flags that indicate characteristics of the route.
- Metric — The routing metric, or cost for the route. A lower number indicates a lower cost and higher route priority.
- Interface — The interface to which packets for this route will be sent. For example, eth0 for interface 0.
This information appears for IPv6 static, dynamic, connected, and BOVPN virtual interface routes.
ARP Table
The ARP table maps IP addresses to the MAC address of each interface.
The ARP table on a Firebox is unique, because the device can do proxy ARP. Proxy ARP enables the device to use the same IP address on three interfaces and to route between them properly. The device does this with a special routing table and proxy ARP requests, which it uses to determine what interface certain IP addresses are connected to.
Flags in the ARP table:
C — Complete entry
M — Permanent entry
P — Published entry
- — If a dash (-) appears in the Mask column, the ARP request/response failed. This could indicate bad cabling, bad Ethernet hardware, or a host that has been removed from the network before the Firebox has removed the host ARP table entry.
An ARP entry usually has a C flag. For a drop-in configuration, ARP entries are usually flagged CMP. If the device is configured in drop-in mode, there are three ARP table entries for each IP address. When a host on any of the networks makes a request for which there is already an ARP entry, the device responds with its own MAC address, then forwards the packet to the correct IP address on one of the other interfaces.
If the HW address is 00:00:00:00:00:00, that indicates that the Firebox was not able to get an ARP response for the IP address. A large number of IP addresses with this IP address can indicate an incorrect interface configuration, or a problem in the network.
Multi-WAN
Information about multi-WAN configuration settings and interface link status appear in these two sections.
DHCP Leases
The DHCP Leases section includes Information about the DHCP client leases on the Firebox that have completed negotiations. The DHCP lease time is the UTC time listed at the start of the report.
In Fireware v12.6.2 or higher, the DHCP Leases section also includes:
Wake On Lan Debian
- Number of DHCP leases in use
- Total number of DHCP leases available in the configuration
DHCPv6 Leases
If you have enabled DHCP for a trusted or optional interface that uses an IPv6 address, information about the leases for those interfaces appears in this section.
Domain Name Servers
The Domain Name Servers section includes the IP addresses of the DNS servers configured on your Firebox.
Dynamic Routing
If you have configured dynamic routing protocols (RIP, OSPF, or BGP) on your Firebox, configuration and status information appears in these sections.
In this example, no dynamic routing protocols are configured on the Firebox .
IPSec Routes
This section includes details about the destination and source IP addresses for the IPSec routes on your Firebox.
Proxmox Enable Wake On Lan
The example for this Firebox does not include any IPSec routes.
If the Status Report for your Firebox does include information about the IPSec routes on the device, the value on the left is the destination subnet and the value on the right is the source address.
For example:
In this example, there is one active route. When you troubleshoot problems with your VPNs, if the VPN does not operate correctly, or operates only intermittently, you might have reached the maximum number of allowed tunnel routes for your device.
Proxy Connection Statistics
This section contains Information on enabled proxies and their connection statistics.
Supports Wake-on D
FireCluster
If your Firebox is included in a FireCluster, information about the FireCluster appears in this section.
In this example, the Firebox is not a member of a FireCluster.
Device System Health
The System Health section includes status and connection delay information for each of the processes that run on your Firebox .
See Also
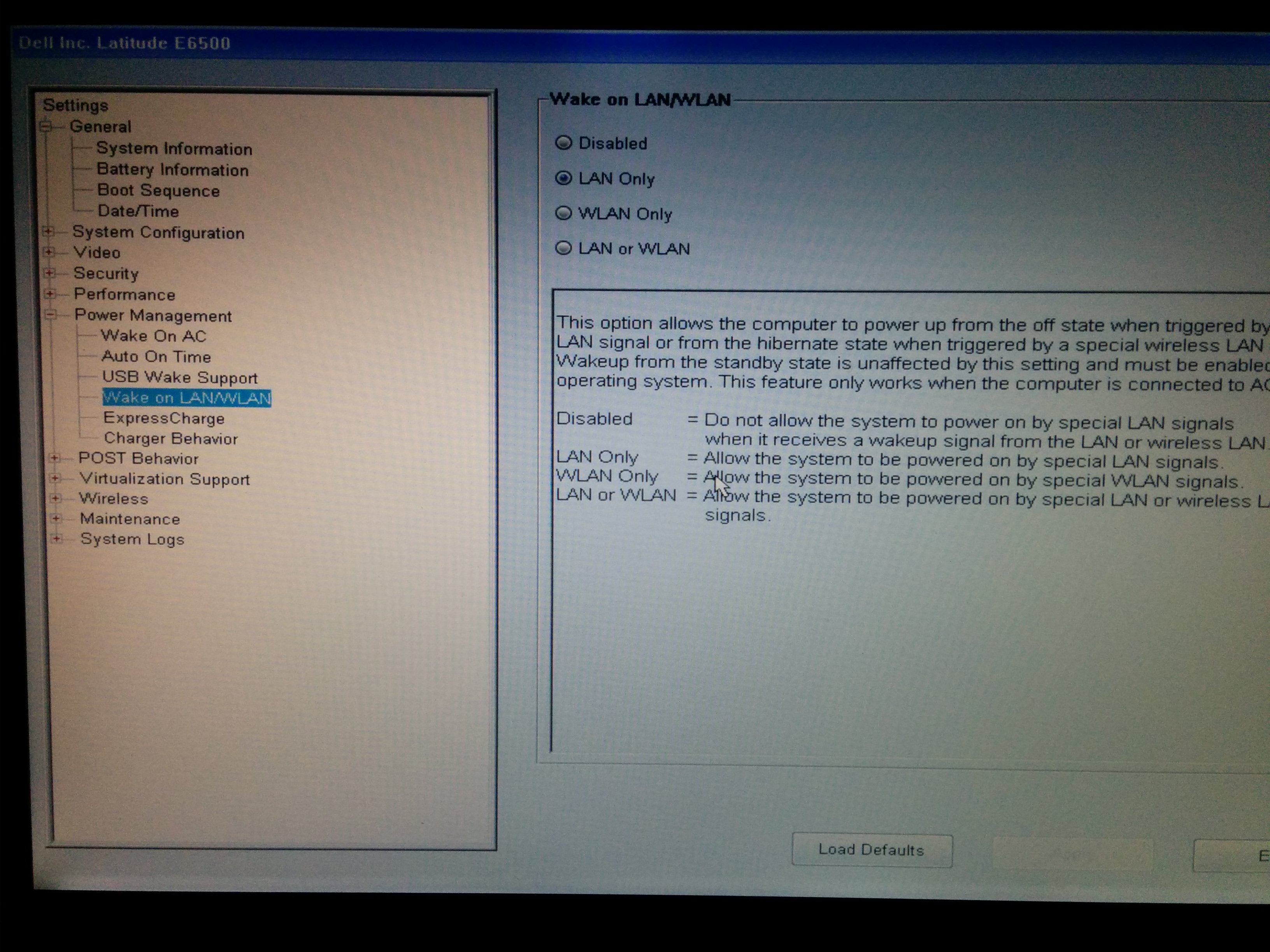
This laptop has wake on lan enabled on bios side.
I checked also from shell
ethtool eth0 | grep -i wake
Supports Wake-on: pumbg
Wake-on: g
I turned off the laptop and tried to wake it from another linux server by
wakeonlan
etherwake -D
and also by an app from a windows 10 pc.
It doesn't turn on!
I looked the /etc/network/interfaces file and there are no option related to wake on lan.
So I wonder if the wake-on get disabled during boot by some instruction I don't know about.
thank you.
